The Diffie-Hellman algorithm inventors were awarded 2015 Turing Award
2016-06-30The famous Diffie-Hellman algorithm inventor Marty Hellman and Whitfield Diffie were awarded 2015 Turing Award. The Association of Computing Machinery (ACM) will hold the annual awards ceremony in San Francisco, California on June 11 th.
In 1976, papers named New Directions in Cryptography published by Diffie and Hellman elaborated the thoughts of public key encryption and electronic signatures, which have now become the most commonly-used security protocol on the Internet and protect our daily network communications as well as trillions of financial transactions.

Development of encryption
Encryption makes it confidential when two parties communicate. The content will be verified by a third party when it is being read or modifying. Method of the earliest encryption turned letters into other symbols and scrambled the alphabetical order in the information. The inventions of electricity and machinery allow machines to do more secured encryption work than people. After the First World War, a lot of encryption machines have developed and been widely used in the Second World War. In the movie The Imitation Game, the machine invented by Turing was the one used to crack encryption machine of German navy, Enigma.

In encryption, a private key is a piece of information used to transfer readable words into incomprehensive gibberish. To encrypt is very similar to lock a lock that needs a particular key to unlock, while decryption is to use the particular key to unlock. In the past, when two groups wanted to establish secret connection, they needed to have the same private keys. Providing these keys, namely the private key management, was the main restriction to the flexibility of encrypted communication.
There are two important drawbacks of symmetric encryption: 1) it needs to transfer the private key in a very secure way; 2) one party can forge a message and send to itself while claim the message is sent from the other party since they have the same private key. In addition, the excessive use of certain private key may give enough encrypted data to enemies so they can use it to study how to crack the encryption system (that is to find out the private key). In order to limit the number of groups who share the private key, the private key is usually shared between two parties (for instance, when three groups of A, B and C are exchanging information, the private key of communications between A and B is different from the one of A and C), which brings extra challenge to private key management.
The birth of public key encryption theory
In the article of New Directions in Cryptography, Diffie and Hellman presented an algorithm which showed the feasibility of asymmetric encryption or public key encryption. In this algorithm, a public key --- not a secret one but can be shared freely --- is used to encrypt, while a private key that’ll never leave the receiving equipment is used to decrypt. Although public key determines the private key, the design principles of asymmetric encryption system make it infeasible to calculate the private key out of public key.
The inverse process of public key encryption brings electronic signature. Message is signed using a private key during transmission. Recipient uses public key of the sender to verify. Compared with handwritten signature, electronic signature is more secure because it will become invalid even if one word of the message is changed while handwritten signature cannot ensure the content won’t be modified.
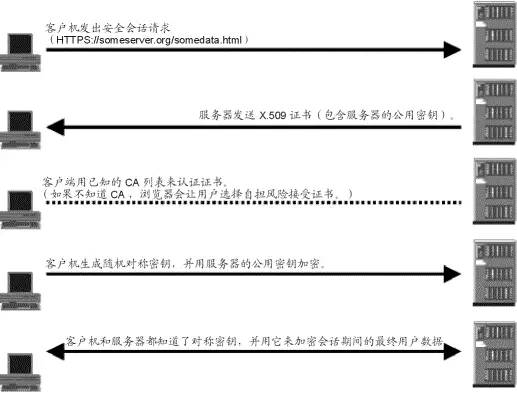
Any Internet user is familiar with using public key encryption to establish secured connection. A typical application is that URL starts with HTTPS, in which the S stands for that network connection uses Secure Transport Layer Protocol to encrypt messages. After public key encryption, a private key of symmetric encryption will be transferred, which is used to encrypt messages.
About Turing Award
Turing Award established in 1966 by the Association of Computing Machinery is to reward individuals who make an important contribution in the field of computers and in commemoration of A.M Turing, the pioneer of world computer science, British scientist and professor of University of Manchester. It is considered as the Nobel Prize in the field of computer science.
The Turing Award was sponsored by Inter Corporation and Google Inc. with a prize of 250,000 dollars before November 13th 2014. After that day, Intel withdrew its sponsorship. Google, on the other hand, increased the reward to 1,000,000 dollars, which is close to the Nobel Prize.
As early as in 2002, Ronald L. Rivest, Adi Shamir and Leonard M. Adleman have been awarded the Turing Award for an implementation of public key encryption, the RSA encryption.

Part of the reference source: Wechat ID Xinzhiyuan
