How does HTTPS encryption prevent traffic hijacking?
2016-04-18Traffic hijacking is the situation of user’s traffic loss caused by using different malware to modify browser, lock the homepage or pop up new window ceaselessly and force user to access certain website. It is an old attack method like the following common advertising popup. Many people have been numb and think it will not cause any loss. However, traffic hijacking can in fact steal information through many imperceptible ways.
Flaws of HTTP protocol make traffic hijacking viable
There are many ways of traffic hijacking. DNS hijacking, CDN invasion, gateway hijacking, ARP attack and Hub sniffer are the common ones. Acquired traffic of different methods differs. DNS hijacking can intercept and capture traffic initiated by domain. Communication directly using IP address will not be affected. CDN invasion is only risky when you browse the webpage or download. All of the user’s traffic is at risk when gateway is hijacked.
At present, traffic hijacking is basically realized by two methods:
1) Domain hijacking
By hijacking the DNS analytic results of domain name and adding HTTPS request to specially appointed IP, servers of client side will establish TCF connection with the attacker’s server rather than the target server. In this way, attacker can steal or modify the information or even forge the target website to conduct phishing attack in extreme case.
2) Direct traffic modifying
It is fixed content insertion to a webpage in data path like advertising popups. In this situation, although the connection between client side and the server is established directly, the data content can still be savagely damaged.
The fundamental cause of traffic hijacking is that HTTP protocol cannot verify the identity of the other party in a communication or verify the completeness of data. If this problem is solved, traffic hijacking will not easily happen.
How does HTTPS encryption prevent traffic hijacking?
HTTPS stands for HTTP over SSL, which means adding a layer of SSL encrypted channel on the basis of HTTP clear text channel. SSL protocol is the network protocol used to solve security problems of transport layer. The core of it is the realization of server identity verification, encryption protection of data and verification of data completeness on the basis of public key cryptography theory.
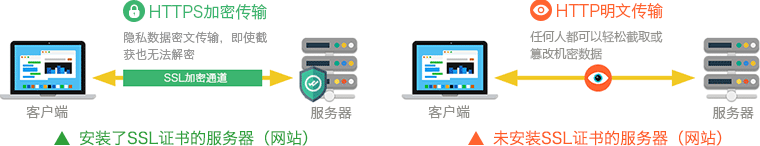
Because SSL protocol provides sever identity verification, the situation of DNS hijacking leading to connection with wrong server will be found and the connection will be terminated. The data encryption and completeness verification provided by SSL protocol solve the problem of key information being sniffed and data content being modified.
How to realize HTTPS encryption
You need to apply for SSL certificate from authoritative CA (such as WoSign CA) if you want to use HTTPS encryption to prevent traffic hijacking. WoSign CA has passed the international certification of WebTrust. Our root certificates are preset into all browsers and mobile terminals. Client side can check the legality of the site’s SSL certificate through the list of trusted root certificate authority in the browser.
WoSign CA provides free SSL certificate of 2-year validation period and 5 domains, which can satisfy the basic needs of the website. All websites can start to use HTTPS encryption at zero cost. What’s more, we also provide OV SSL certificate and EV SSL certificate of higher levels, which verify and present the real identity of the website’s owner.
After successfully applying for WoSign SSL certificate, user can directly deploy the certificate in Web server. There is comprehensive guidance of server certificate deployment. If you are user of Aliyun, the trouble will be saved. You can choose and purchase certificate on Aliyun platform.
The combination of Aliyun and WoSign SSL certificate allows you to deploy HTTPS encryption in one click
Combined with WoSign SSL certificate, Aliyun introduced cloud shield certificate service to provide application services of SSL certificate application, validation and deployment.
Aliyun users can purchase WoSign SSL certificate online at https://www.aliyun.com/product/cas.
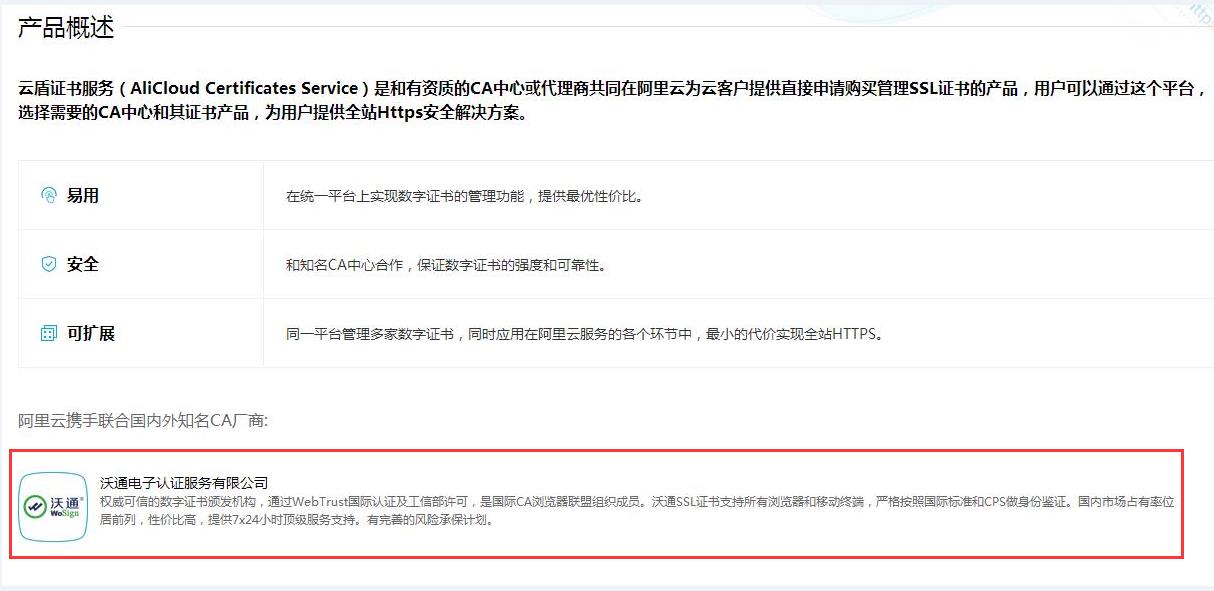
After the application being approved, choose the cloud product that needs to deploy HTTPS encryption and upload the private key and “push”. Then the deployment of SSL certificate is completed. At present, Aliyun cloud shield IP of high defense has already been supportive of SSL certificate’s push service in one click. Products of cloud shield WAF firewall, CDN, SLB and cloud mailbox will in succession be supportive of this function.