CSR Generation Instruction - Tomcat and J2EE Application Server
An Important Note Before You Start
By far the most common problem users have when going through this process is related to private keys. If you lose or cannot access a private key, you cannot use the certificate we issue to you and will need to request a free reissue. To ensure this never happens, we advise that a backup of the private key file is made and that a note is made of the password that is used to protect the export of the private key.
The utility "keytool" that you use to generate the private key (keyEntry) and CSR comes with the Sun JDK toolkit. If you do not have JDK installed please download it from the following link: http://java.sun.com/J2SE/downloads.html,We recommend that the latest version be used, which is 1.5.0.
The following sequence of commands will generate a keystore and keyEntry. Tomcat currently supports JKS and PKCS#12 format keystores. The JKS format is Java's standard "Java KeyStore" format, and is the format generated by the keytool command-line utility which is packaged in the JDK kit. The PKCS#12 format is a general format which can be converted using the Openssl toolkit. The following instructions make use of keytool only.
1. Generate a keystore and keyEntry
Please type the following command at the prompt:
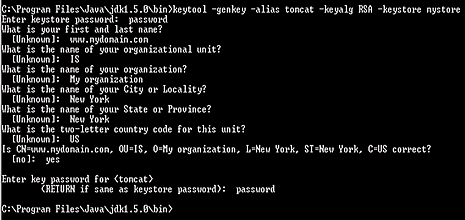
keytool -genkey -alias [keyEntry_name] -keyalg RSA -keystore [keystore_name]
Note: If you do not specify a keystore (-keystore omitted from the command) name, the keystore will be saved to your local profile directory as a .keystore file (i.e C:\Documents and Settings\your name\.keystore)
When you execute this command you will be prompted for a keystore password. The default password used by Tomcat is "changeit" although you can specify a password of your choice.
The term "First and last name" is X.509 speak for the name that distinguishes the certificate best, and ties it to your Organization. Enter your exact host and domain name that you wish to secure. Example: If you wish to secure www.mydomain.com, then you will need to enter the exact host (www) and domain name (mydomain.com) in this field. If you enter mydomain.com then the certificate issued to you will only work error free on https://mydomain.com. It will cause a certificate mismatch error when you or your users access the domain via https:// www.mydomain.com.
Enter your country, state or province and locality or city. You should enter the company name as it appears on your official company registration documents. The organization unit is optional, we verify and authenticate the company name and not the organization unit. To skip the organization unit (OU) field please press enter on your keyboard.
Finally, you will be prompted for the keyEntry password, which is the password which protects the private key. Please specify the same password for the keystore and the keyEntry or else you will receive the following error message when you restart the Tomcat engine: java.security.UnrecoverableKeyException: Cannot recover key
2. Generate the CSR
Please type the following command at the prompt:
keytool -certreq -alias [keyEntry name] -file request.csr -keystore [keystore name]
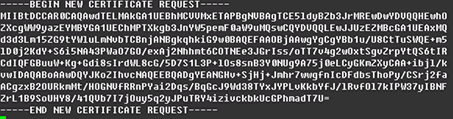
The CSR will be saved to your JDK/bin directory. You have now created a public/private key pair. The private key (KeyEntry) is stored inside the keystore in the JDK/bin directory and is used for decryption. The public portion is sent to WoTrust in the form of a Certificate Signing Request (request.csr), and will be used by your users to encrypt the data they send to your site. The Certificate Signing Request (CSR) looks something like this:
3. Backup your private key
Please backup your keystore file and make a note of the password. A good choice is to create a copy of this file onto a diskette or other removeable media.
4. Start the certificate request process
To submit the CSR to WoSign for processing you should start the certificate enrollment process.
